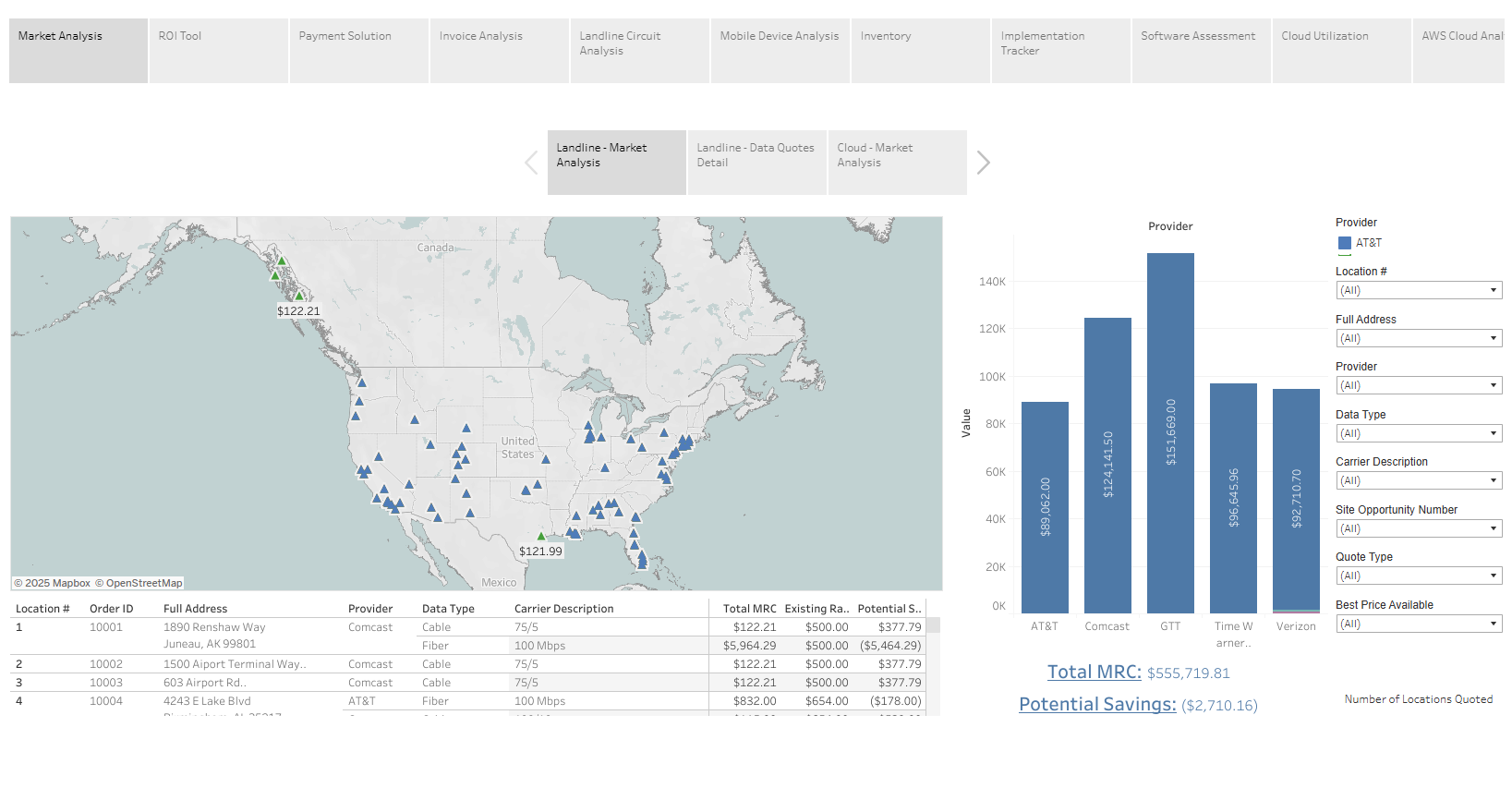
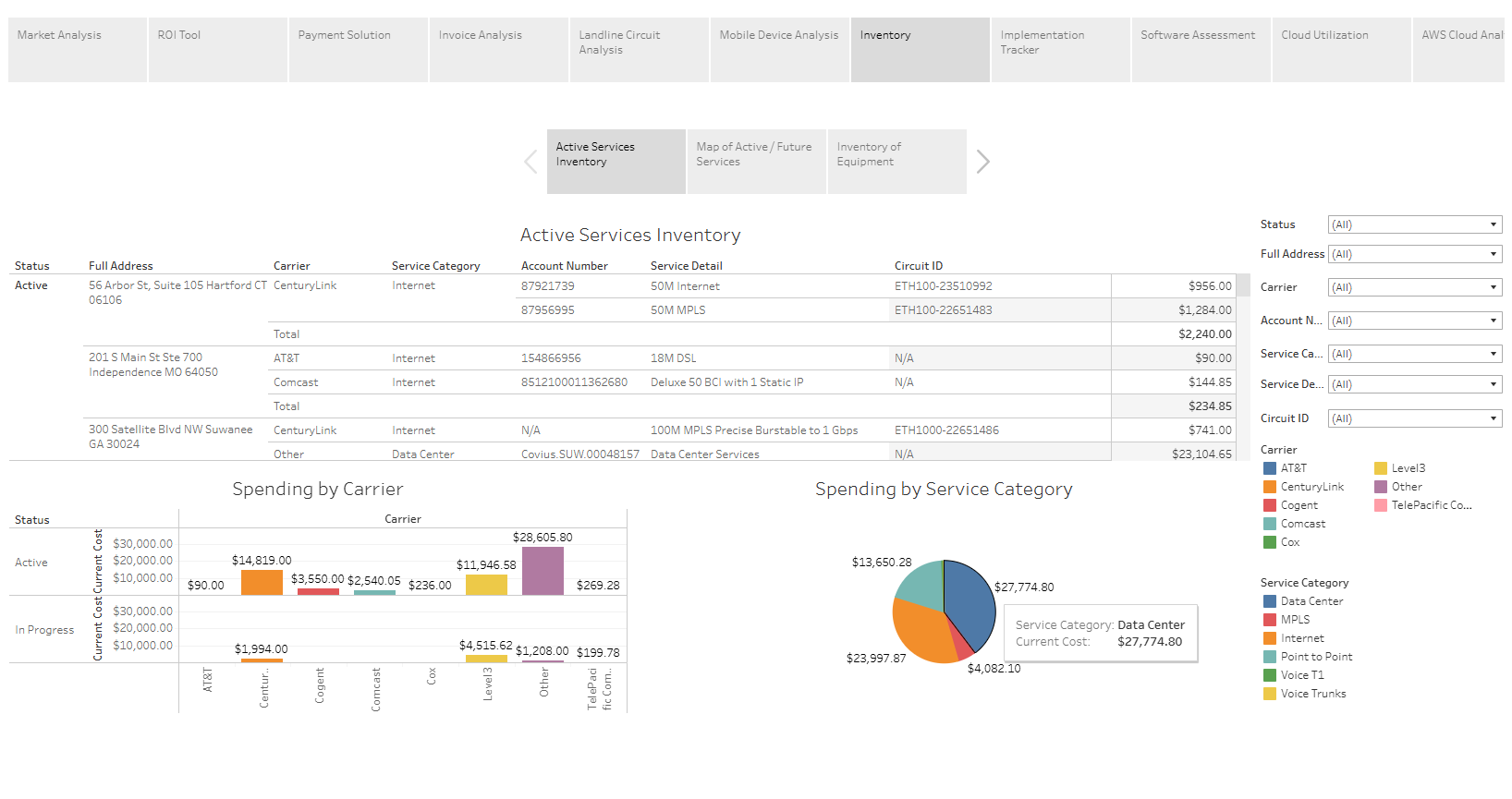
24HR Quick Quote
Please provide details about how we can help. Include any business addresses.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Close
24HR Quick Quote
Please provide details about how we can help. Include any business addresses.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Close

.png)













.png)

.png)
.png)
.png)
.png)